<DISCLAIMER> I started writing this post in 2015 but never finished it, mostly because i enjoy riding a motorbike a lot more than i enjoy spending hours spell-checking something almost no-one will read. Sorry once more, will get some new more relevant stuff here soon, but for now feel free to read this..</DISCLAIMER>
In a sense this entry don’t really belong at this blog as no actual hacking was ever needed so I am sharing this as more of a security advisory for someone that never decommission a server.
After a wet night in the bar with the guys I found a computer sticking out of a waste container on my way home. I noticed the IBM X-series logo which made me disregard that it was covered in an inch of snow and I dragged it home.
It turned out to be a X3200 tower, running a Xeon E3400 cpu at 1.8 ghz, 4 gb of ddr2 memory, 2 sata-mirrors. 80gb for OS, one 500gb mirror for data, by the look of it.
The hardware
After a proper drying I plugged it in. Power icon was blinking green but pushing the button did nothing. I measured the button using a multimeter, but the switch itself worked. I found a “Power On” jumper on the motherboard and once shorted the machine rev’ed up its fans but never let ACPI kick in to lower the RPM of the fans, nor initiating BIOS. Monitor indicated no VGA signal either.
I was fiddling with jumpers for quite some time, I reset the CMOS and noticed that when i moved back the jumper to Disabled that the box twitched to life. The monitor flickered up and the blue iconic X-series logo filled the screen, with a few beeps and warnings about the CMOS battery having low voltage it came back to life. Unfortunately I had no disk connected to the system at this point and it would take another 45 minutes before I succeeded to do it again. After hours of trying to streamline the process of getting it booted the recipe for success seems to be:
Use the Power ON jumper for 20 seconds. Pull the power-cord to the server. Enable CMOS-reset with the jumper on the motherboard. Put the power-cord back in. Leave the server for 20 minutes with the CMOS-reset ON. Then…. pull out the CMOS reset jumper :) BOOM! The server boots Windows 2003: A real man-OS!:
Not being a huge fan of spending 20 minutes on booting any machine I kept looking for something simpler. Trickling pin 2 and 3 on the WOL-connector on the network adapter did make the power-led on the motherboard flicker but once more didn’t start the machine up.
I never mentioned how restless I am as a person in this blog, but for people who know me that is a fact. What I did mention was that both OS and Data disks where both in a mirrored configuration, once this was confirmed in the BIOS, it allowed me to snatch one disk of each mirror to be able to see what was lurking on the sectors while waiting for the server to get ready for it’s next boot.
“This is Windows.. I know windows!”
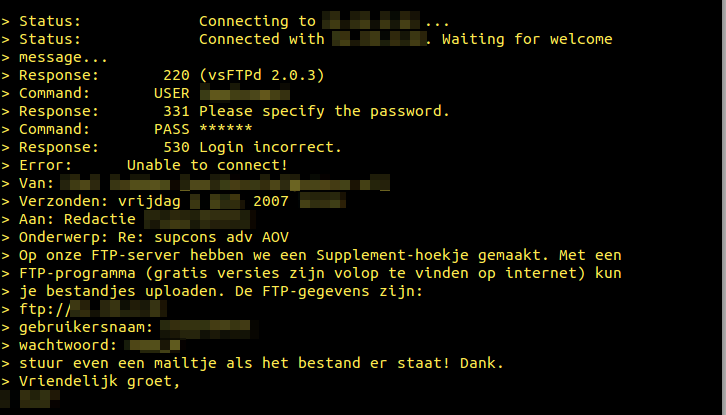
I hooked up the OS-drive with a SATA-to-USB-dongle and mounted the NTFS partition on my linux-laptop. The 80gb drive was divided into 2 partitions. 21gb for OS and a 55gb labeled EXCHANGE. I was happy to see no attempt at encrypting (or destroying the drives for that matter) were made but I guess if I saw such attempts I would be even more curios to see what they tried to hide from me. I am far from an expert on Windows these days but it didn’t take long to locate the the email data-directory belonging to the email exchange server, that the partion-name indicated would be there.
TIL that e-mails are stored in clear-text in Exchange 2010.
Curious about who owned the machine before me I started reading mail after mail. A picture slowly dawned on me. Some kind of medical related, pedicure, new age thing, something? I was intrigued.
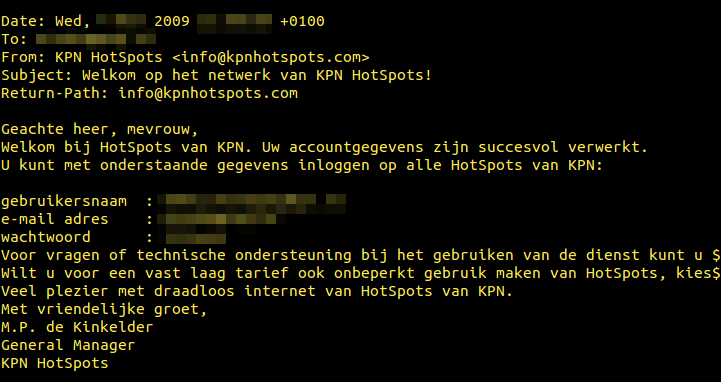
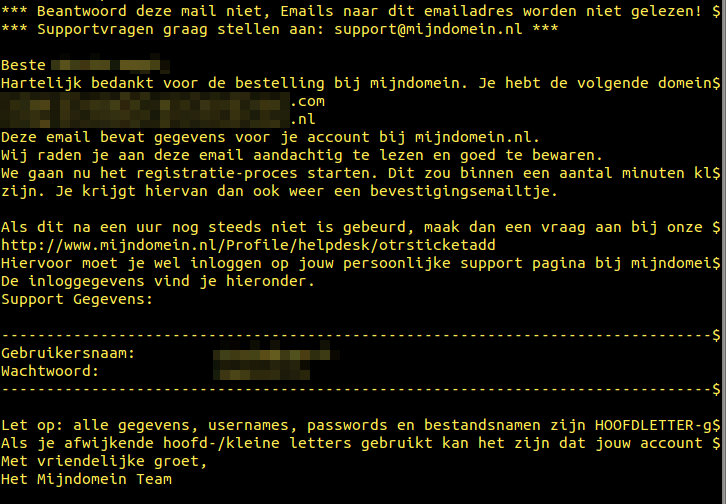
Using standard un*x tools like cat, grep and more I could see every email sent and received from 2007 to 2011. Just for the fuck of it I greped out 20 lines surrounding the word “Password” and “Wachtwoord” and piped it to two files.
Now, I understand a tiny non-IT company can mess up and send out clear-text password..
..but KPN is the stately owned phone-company in Holland, and should know better :)
Hosting companies don’t seem to mind keeping it simple.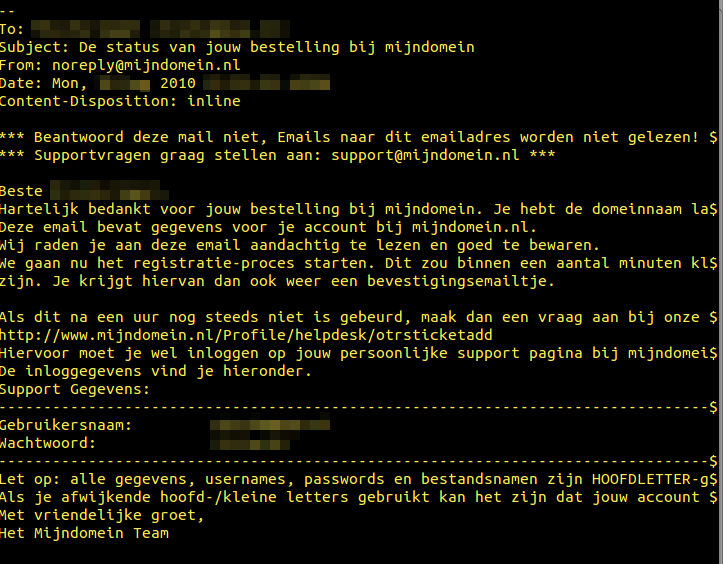
I guess it’s up to their customer not to keep the same 6 character-passwords year after year. I am however convinced mijndomain.nl has changed practices on this topic anno 2015?
I want to point out that I never tried to use any of the passwords to verify if they worked or not as that would be highly illegal. Additionally some logins were to patient care systems, making it utterly unethical to touch. I did however google the companies, visited their homepages to get a greater idea of exactly what they did and how they connected to the company who’s server I stumbled into. Needless to say i read up on the company itself, which still exists.
Seeing many passwords never changed during the years and many were frequently reused between different systems, i feel safe to bet some of them still work. But I wasn’t really that curious about the passwords and continue exploring the rest of the emails. Who were these guys?
Slowly the picture of the prior residents cleared. They had their own little newsletter, were selling subscriptions, seemed to be holding courses, involved in Integrative medicine (Never heard of it before but I am a skeptic. A fast search through all mailboxes got me bored. Almost all of the emails in all the email-boxes was work-related, how boring of them. You can only read so many of someones emails before you need to do something else.
I started checking out the Data drive. It turns out this was not only the Exchange server in their tiny infrastructure. It also carried their Domain controller and roaming home folders. I searched the user home folders, starting with the Administrator account. I could not believe my eyes..
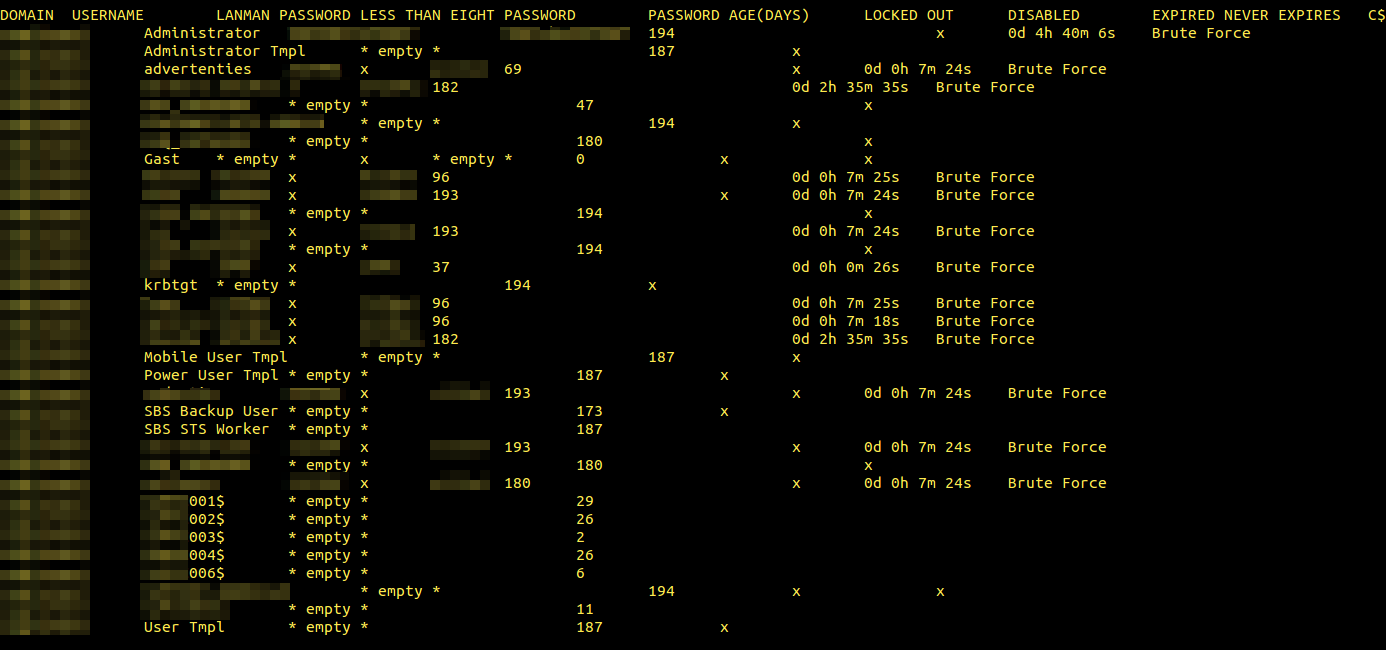
Someone already brute-forced the server and the result files were still there :)
Worth to mention is that it took 7m24s to brute-force the computer-knowing layout guy’s password, while it took 2h35m35s to crack he person I assume works in accounting.
Almost all passwords followed the same standard: X123Y4, where _123_4 never changes between users and the letters did to a certain degree. I can only assume these passwords were set by whomever delivered the system and never changed.
One user seemed to have changed his password but instead of setting a better password he went with a 4 digit only password, which was cracked in 26 seconds.
Initially i assumed it was the Administrator’s own pen-tests but looking through the mail again, it seemed they had been hacked around the same time this password file was created:
One guy seem to enjoy the peace it brought to the office and point out that it is Friday the 13th. Some external partner responds “Digi-missery”.
In the meantime the server booted up again
The server was finally booting up on two single disk mirrors. My eyes glittered in the LCD-light. I would finally get to hack something.. or.. well.. I had the passwords to all accounts already, so technically still no hacking. But i would at least get to enter a username and password and feel like a hacker. Nope, machine seemed to have a registry hack and automatically logged in as Administrator, but something hung it after that. As i didn’t want it to start connecting out on the internet i just hooked it in to a switch without uplink.
I have to say I was a bit surprised to find the brute-forced password file, but not as surprised as I was about to become. Turn out this machine also hosted several windows shares.
One was most likely used by their HR, as i could find ALL information about people working there, like digital copies of their contracts and dismissals.
Another share contained a lot of access databases. Their complete customer-database, sales records, lists of prospect customers and tons of PDF-material about their products.
With the data i had at this point, i could map the whole company up on a time-line, seeing who started when, what they got paid, when they left. I could build a visual picture of who emailed who, which seller caught the big fish and who was just complaining about work while slacking. With almost 10GB of email, 500GB of data and no real idea of where I wanted to go out of it, this blog-post got hanging mid-air. It would take a year to go through it all. And most of it way to fucking boring to plow through.
I kept looking and found pictures from a few events their company participated in. Some of the pictures were named after who they depicted, allowing me to put a face on most of the names from emails i had been reading. It almost felt like i knew the people at this point. I was about to get way closer than i wished for.
I explored the the data-drive and found a backup windows share. Turns out this server was also used by some of the people to back up their laptops, and some of them were very.. blunt.
One of the sales guys, which i recognized from pictures i found from a kickoff he went to was obviously gay. I don’t claim to be able to spot a gay guy, nor do i judge anyone being gay but this guy had tons of pictures of him and a friend fucking a tiny Asian man making me pretty sure this was the case with this guy. Among the data he traveled with (and cared enough to backup) was GB’s off piss-porn.
I wanted to finish up this post a while back, but as i mentioned, I had NO IDEA of what to do with this. Obviously i would never attempt to use it against the company or any of their employees, but the next guy to find this might not be as friendly as I am.
Bits of advise, anyone?
No matter what you Think is on a computer you are getting rid off, small pieces of your life’s puzzle are stored on that machine. May it be in your internet-cache, in your cookies or from RAM in a swapfile. Someone with the right motivation or amount of interest will be able to scavenge it and use it against you.
If you ever toss away anything with a NAND-circuit (like a broken cellphone that contained naked pictures of your gf), unscrew/drill out the screws and use the a car battery charge to short every circuit on the board, making sure who ever tries to retrieve the data, gets a run for his money.
If you ever toss a PC with a harddrive, remove the drive, smash it to pieces with a hammer or drill right through it a few time. It only takes a few minutes, and you know for sure you are safe from 99.9% of people as curious as me.
If you are decommissioning a combined mail-server, file-server, piss-porn-repository, containing all your financial statements, all your customer information, every edge you have on your competition: For the love of Science, make sure no-one can just pick it up and just power it on.